Introduction
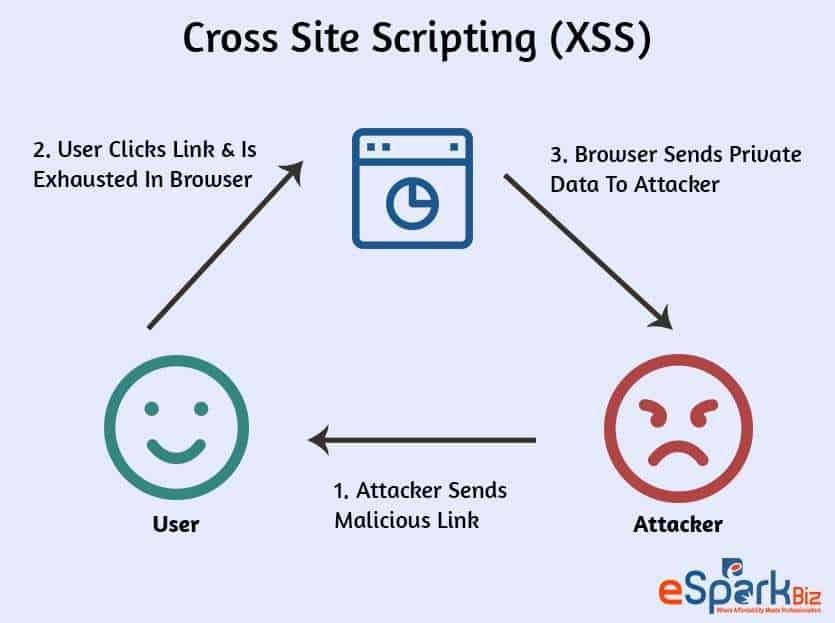
Image: www.esparkinfo.com
In today’s interconnected world, web applications have become integral to our lives, handling sensitive data and facilitating critical transactions. However, malicious actors are constantly devising ways to exploit vulnerabilities in these systems, putting user information and financial assets at risk. One of the most prevalent attack vectors is Cross-Site Scripting (XSS), a vulnerability that allows attackers to inject malicious scripts into a web application. This can lead to devastating consequences, including data theft, account hijacking, and malware distribution. For Java developers, understanding and addressing XSS vulnerabilities is paramount. In this comprehensive guide, we will explore the nitty-gritty of XSS, its impact, and effective prevention techniques.
Demystifying Cross-Site Scripting
Cross-Site Scripting, or XSS, is a type of web security vulnerability that enables an attacker to inject malicious scripts into a web application. This malicious code can be executed in the victim’s browser, giving the attacker access to sensitive information such as cookies, session tokens, and even control over the user’s account. XSS attacks can be categorized into three main types:
- Reflected XSS: The malicious script is included in a request to the server, which then sends it back to the client in the response. The script is executed in the victim’s browser when the response is loaded.
- Persistent XSS: The malicious script is stored on the server-side, typically in a database. When a victim visits a page that includes the stored script, it is executed in the victim’s browser.
- DOM-based XSS: The malicious script is injected directly into the Document Object Model (DOM) of the web application. This can be achieved through event handlers or by modifying HTML elements.
Consequences of XSS Attacks
XSS vulnerabilities can have severe consequences for both users and organizations:
- Data Theft: Attackers can steal personal information such as credit card numbers, passwords, and user profiles.
- Account Hijacking: Attackers can take control of user accounts, allowing them to make unauthorized transactions or send malicious emails.
- Malware Distribution: Malicious scripts can download and install malware onto the victim’s computer, compromising the entire system.
- Website Defacement: Attackers can use XSS to alter the appearance of a website, causing reputational damage and disrupting business operations.
Prevention Techniques for Java Developers
Fortunately, there are effective techniques that Java developers can employ to prevent XSS vulnerabilities:
- Input Validation: Thoroughly validate all user-provided input to ensure it does not contain malicious code. Use regular expressions or filtering libraries to detect and reject potential threats.
- Output Encoding: Encode all user-provided input before displaying it on the web page. This prevents the browser from interpreting the input as executable code.
- HttpOnly Flag: Use the “HttpOnly” flag on session cookies to prevent them from being accessed by client-side scripts.
- Content Security Policy (CSP): Implement a CSP to restrict the execution of JavaScript from untrusted sources.
Expert Insights and Actionable Tips
Renowned security expert Mike O’Dell advises, “The key to preventing XSS vulnerabilities lies in a layered approach to security. Combine input validation, output encoding, and CSP to create a robust defense mechanism.”
Security analyst Sarah Jones emphasizes, “Regularly test your web applications for XSS vulnerabilities using automated tools and manual penetration testing. Early detection and remediation are crucial.”
Conclusion
Cross-Site Scripting vulnerabilities pose a serious threat to the security of web applications. By understanding the different types of XSS attacks, their consequences, and the effective prevention techniques available, Java developers can proactively safeguard their applications against these threats. By implementing rigorous input validation, output encoding, and adopting industry best practices, they can create secure and trustworthy applications that protect user data and mitigate the risks associated with XSS vulnerabilities. Let’s commit to the highest standards of web security and ensure that our digital interactions remain safe and protected.
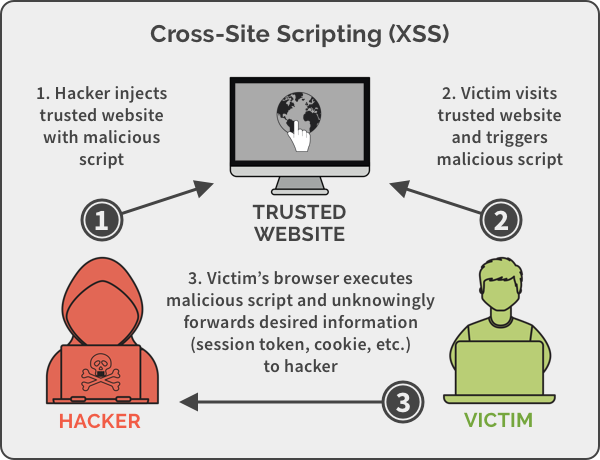
Image: www.business2community.com
How To Fix Cross Site Scripting Vulnerability In Java Example